 1-800-805-5783
1-800-805-5783 
Microservices, a software development technique that structures an application as a collection of loosely coupled services, each running its process and communicating through APIs, has gained immense popularity recently due to its potential for enhancing scalability, flexibility, and fault tolerance. However, the need to handle microservices security challenges grows as the number of microservices within a system increases.
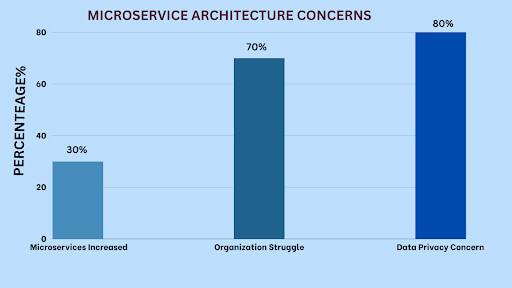
For instance, a study by IBM, a leading technology company, found that the average number of microservices in a system has increased by 30% in the past two years. Microservices enforce security by shielding private information from unwanted access.
In other words, microservices security divides huge applications into minor, independent services that interact with each other using APIs.
A Gartner survey found that 70% of organizations need help managing the complexity of their microservices security. Each microservice is supposed to be responsible for a particular business function and can be developed, deployed, and scaled independently.
This blog will cover must-know strategies and best practices for implementing proper microservices security and access control in microservices security. We will discuss authentication, authorization, API gateways, and data encryption to secure your microservices application from impending threats.
Importance of Security in Microservices
Microservices security raises excellent security concerns due to the increased number of components involved and their interactions with one another. However, this also introduces more vulnerabilities because breaching a single microservice can quickly compromise an entire system.
With 80% of organizations identifying data privacy as a top concern in microservices security, robust security measures are more critical than ever. As IT professionals, software developers, security analysts, and decision-makers, your role in ensuring data protection is paramount.
Microservices security creates several unique challenges:
Increased attack surface: Greater proliferation of microservices means more possible ways for an attacker to attack.
Complexity: Microservices security complicates the process of discovering and treating security defects.
Inter-service communication: This is, in general, prone to microservices security risks if properly not under protection.
Data privacy: Microservices often handle sensitive data that has to be kept out of unauthorized access.
Third-party dependencies: The third-party libraries and services applied in microservices bring their security risks, necessitating a cautious approach to their integration.
Because of microservices’ distributed nature, introducing new security challenges into an application can be difficult. Ensuring integrity, confidentiality, and availability within microservices applications requires an emphasis on microservices security.
Authentication means the validation of identity for a user or system. This ensures that access is given only to those whose specific authorization allows access to an application. Some common ways of authenticating include
Username and password: This is the classic authentication method whereby the user inserts a username and password.
Token-based authentication: This more modern authentication method involves using tokens to authenticate users and systems. Tokens are usually issued from a central authentication server and can be time-limited or revoked.
OAuth: An open standard authorization that grants third-party applications access to user data.
Authorization is the procedure of determining what actions a user or system can perform. It checks whether a particular user has the proper authority to perform certain kinds of operations or has access to certain types of resources. There are different ways in which authorization can be implemented:
RBAC: This is permission based on a person’s role or membership in certain groups.
ABAC: Activity-based access control grants permission based on user, resource, and environment attributes.
Policy-Based Access Control (PBAC): This is meant to define the policies entailing the type of access granted to what users or systems to which resources under what circumstances.
Encryption refers to transforming data into code that unauthorized people cannot read. It assists in preventing unwanted access to the exposure of sensitive data. And exposure. Some of the standard encryption algorithms are as follows:
The same key is used for both encryption and symmetric decryption in symmetric encryption.
Asymmetric encryption involves using two types of keys: a public key and a private key. The public key encrypts data, whereas the private key is used for decryption.
Hashing: The process by which an arbitrary input of data is converted into a fixed-size digest. It is usually used for password storage and verification.
Decrypting can be defined as the reverse encryption operation for recovering the data.
Access control mechanisms in a microservices security control access to resources and services. Some common mechanisms include the following:
API gateways, a key component in microservices architecture, act as entry points for all requests to the microservices security and can enforce the access control policies.
Service meshes provide a layer of abstraction between the microservices; they handle tasks like service discovery, load balancing, and microservices security.
Token-based authentication enables access control by limiting the extent of access granted to a user or system.
Implementing microservices security measures with appropriate authentication, authorization, encryption, and access control shall protect microservices applications against various security attacks and grant full assurance about data confidentiality, integrity, and availability.
Thus, it can use robust authentication, authorization, encryption, and access control to ensure the security of microservice applications by inhibiting data breaches and breaches of confidentiality, integrity, and availability.

Let us explore some of the most common threats you would come across:
API Vulnerabilities: Injection attacks, such as SQL injection, command injection, and cross-site scripting (XSS), can result in unauthorized access or the execution of malicious code.
Poor authentication mechanisms allow unauthorized access.
Sensitive Data Exposure: This is a no-brainer. Transmission of sensitive information by misfortune in API responses can lead to data breaches.
Broken Access Control: Lousy activity access control may allow illegitimate clients to access restricted assets.
Data Breaches Data Exposure: Insecure APIs or putting away components may reveal touchy information.
Unauthorized Access: Surprise access to microservices compromises information security and protection.
Insider Threats: The most colossal danger is the data-thriving workers.
Excess Resource Utilization: Deluging microservices with spurious traffic may further reduce services.
DDoS Attack: Coordinated attacks from several sources may overwhelm microservices.
The Numbers Say It All
In fact, according to OWASP, API security remains one of the primary issues businesses face because injection attacks, broken authentication, and sensitive data exposure are some of the most common web application microservices security risks.
However, if that is not enough, an IBM study claims that the global average cost of a data breach in 2023 will be an outstanding $4,350,000. DDoS attacks, including those against critical infrastructure and government services, continue to rise.
So, how can you enhance your microservices security?
API Security: Perform strong authentication and authorization, validate input data, and prevent injection attacks.
Data Protection: Encrypt data at rest and in transit, implement access control, and monitor for unauthorized access regularly.
Dos Protection: Employ DDoS protection strategies like rate limitation and traffic filtering.
Security Testing: Security testing should be performed periodically to discover and patch vulnerabilities.
Employee Security Training: Train your team on best practices and insider threats.
By responding to these security challenges, you will have secured your microservices and ensured the confidentiality, integrity, and availability of your data.
Microservices security offers flexibility and scalability and opens the floodgates to newer security challenges. Therefore, it is crucial to execute robust measures to safeguard your microservices applications from potential threats. Here is a breakdown of some key strategies.
API Gateways: The Centralized Protector
The best explanation for API gateways would be the metaphor of the entrance to a nightclub, where a big guy at the door controls who gets in and what each one can do.
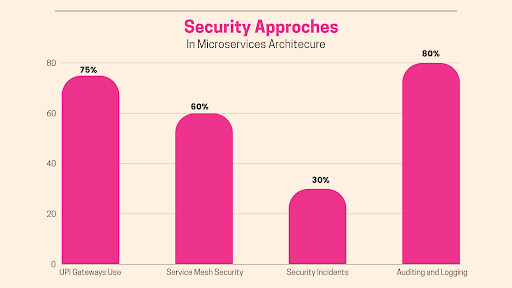
A study by Gartner found that 75% of organizations use API gateways to secure their microservices security. You can place an API gateway at the entry point in your microservices environment so that:
You centralize control: Observe all the incoming traffic and enforce microservices security policies.
You can authenticate and authorize: Permit only those users authorized to access specific microservices.
It does this by including:
Traffic control: Abusive and attack traffic is kept under a threshold by limiting requests.
Version management: Versioning is used to maintain compatibility between different versions of your APIs.
Service Mesh: The Invisible Guardian
Think of a service mesh as an invisible corps of security guards watching your microservices. It encrypts, authenticates, and authorizes without changing a line of code in any of your services.
A survey by CNCF found that 60% of organizations use service meshes for security purposes. In other words, you can keep working on your application while the service mesh handles nitty-gritty details concerning security.
Identity and Access Management (IAM): The Key to the Kingdom
IAM is the master key that controls access to your microservices. It does some work for you, helping you manage users, allow single sign-on, and define permissions.
This will mean that you intend to keep track of who has access to your system, have users log into multiple microservices with a single set of credentials, or specify what a user can do within the environment of their microservices. A study by Forrester found that organizations using IAM solutions experienced a 30% reduction in security incidents.
Encryption: Locking Down Your Data
Encryption is the lock on your treasure chest, protecting your data from unauthorized access. Through encryption, you ensure confidentiality and security both at rest and in transit. A study by IBM found that 90% of organizations believe that encryption is essential for protecting sensitive data in microservices security.
Auditing and Logging: Digital Watchdog
A study by PwC found that 80% of organizations believe that auditing and logging are critical for maintaining a secure microservices security. Auditing and logging are like security cameras watching over your microservices environment they help you in.
They will be entitled to threat monitoring, incident investigation, and regulatory compliance observance. In return, security breaches of microservices applications will be avoided. Security is a continuous process; therefore, constant reevaluation and updates of practices will be required to handle emerging threats.

Microservices security offers many benefits, including scalability, flexibility, and fault tolerance. But, its distributed nature also introduces new security challenges. You must follow strong security measures to keep your microservices applications safe.
1. Least Privilege Principle:
2. Regular Security Audits:
3. Patch Management:
4. Secure Coding Practices:
5. Incident Response Planning:
Following these best practices can make your microservices applications more secure and protect your business from threats.

Netflix, Amazon, and Uber are examples of companies that did quite well in implementing security in their microservices environments. They learned a lot from them and can teach us valuable lessons.
API gateways, tokens, and a service mesh regulate Netflix access and data protection. For Amazon, permissions are controlled by IAM, KMS encryption, and WAF web security. Uber relies on OAuth to secure its users’ data, adding data encryption and frequent security testing.
But remember, even the most significant companies sometimes make mistakes. Security breaches happen, and that is how one learns from them. Here are some key takeaways:
• Implement security early: Think of security from the beginning rather than as an afterthought in your project.
• Keep scanning for issues: Security threats constantly evolve, so one must monitor systems periodically for vulnerabilities.
• Plan for emergencies: A good plan makes responding promptly and successfully to a security breach easier and minimizes the damage.
• Staff training: Ensure each employee is taught to maintain secure data.
Be careful with whom you work with. Ask questions about the security of third-party companies that handle your business.
Microservices security refers to the strategies, patterns, and mechanisms used to protect individual services within a microservices architecture. Since microservices operate as independent components, security in microservices requires enforcing security at multiple levels, including communication between services, access control, and data handling. It involves implementing authentication, authorization, and encryption for each service while maintaining the overall security posture of the system.
The biggest challenge in microservices security is managing distributed security. Each service has its own security requirements, and as the number of services grows, maintaining consistency and managing the complexity becomes difficult. Ensuring that security in microservices remains centralized and follows microservices security patterns like OAuth for authentication or API gateways for access control can help mitigate risks, but the challenge lies in securing communication, data, and user access across distributed systems.
To protect your APIs and microservices, you need to implement strong microservices security patterns like token-based authentication (e.g., OAuth 2.0), API gateways for traffic management, and encrypted communication using SSL/TLS. It’s important to also enforce fine-grained access control through role-based access control (RBAC) or attribute-based access control (ABAC) to ensure that only authorized users can access certain services. Additionally, each microservice should be isolated to minimize the risk of lateral attacks.
SSL (Secure Sockets Layer) or TLS (Transport Layer Security) works by encrypting the communication between services to ensure that data transmitted over the network is secure. In microservices, each service might communicate over the network with others, so securing those communications with SSL/TLS is crucial. This prevents attackers from intercepting sensitive data. SSL is often combined with microservices security patterns such as mutual TLS (mTLS) for verifying both the client and server’s identity to establish trusted and secure communication channels.
Microservices security is finding its way into modern software development due to its scalability, agility, and fault tolerance. However, microservices’ distributed nature presents a host of unique security-related challenges in securing sensitive data and ensuring the integrity of microservices-based applications.
Generally speaking, an organization can reduce these risks by implementing a comprehensive security strategy covering authentication, authorization, API security, data encryption, network security, logging and monitoring, and patching. This is how one could keep a microservices infrastructure resilient. By continuously monitoring and improving security, there are better chances of addressing emerging threats and maintaining microservices security measures.
If security is emphasized from the beginning of the development lifecycle, then organizations can achieve all the benefits microservices provide with minimized risks.
[x]cube LABS’s teams of product owners and experts have worked with global brands such as Panini, Mann+Hummel, tradeMONSTER, and others to deliver over 950 successful digital products, resulting in the creation of new digital revenue lines and entirely new businesses. With over 30 global product design and development awards, [x]cube LABS has established itself among global enterprises’ top digital transformation partners.
Why work with [x]cube LABS?
Our co-founders and tech architects are deeply involved in projects and are unafraid to get their hands dirty.
Our tech leaders have spent decades solving complex technical problems. Having them on your project is like instantly plugging into thousands of person-hours of real-life experience.
We are obsessed with crafting top-quality products. We hire only the best hands-on talent. We train them like Navy Seals to meet our standards of software craftsmanship.
Eye on the puck. We constantly research and stay up-to-speed with the best technology has to offer.
Our CI/CD tools ensure strict quality checks to ensure the code in your project is top-notch.
Contact us to discuss your digital innovation plans, and our experts would be happy to schedule a free consultation.